MQP:Java Security
|
Overview
Java, since 1.2, has some interesting security features related to access control. There are many security features dealing with Java's class loaders, assuring that the code is from a trusted source, and certificate/key management that will not be discussed here. These features are important to Java's overall security design, but are not important to the scope of this project.
This article focuses on the design and usage of Java's ability to provide fine-grained access control to features such as file access, socket communication, program configuration, and security configuration.
More work needs to be done on this page, so if somthing is missing, don't be surprised
Security Architecture Overview
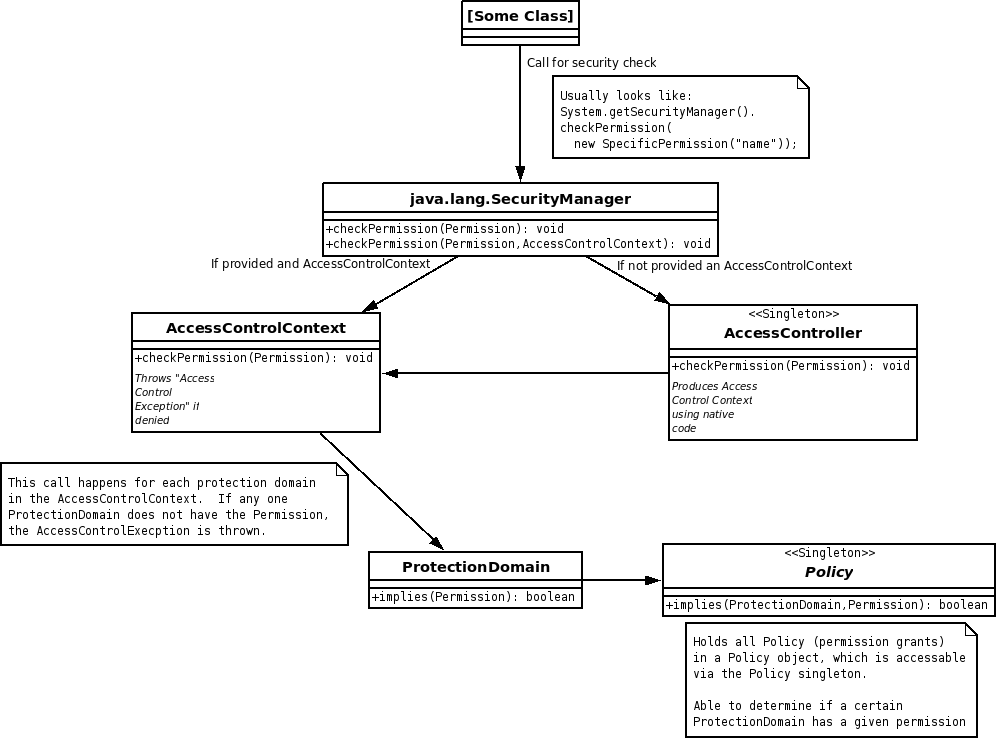
Most of Java's security classes reside in the java.security package. For the purposes of this section, if no package is noted, java.security can be assumed.
Permission Classes
- Permission (Abstract Class)
- Defines a type of permission
- Extensions of this class include:
- java.security.
- UnresolvedPermission
- BasicPermission
- SecurityPermission
- AllPermission
- java.io.
- FilePermission
- SerializablePermission
- java.net.
- SocketPermission
- NetPermission
- java.lang.
- RuntimePermision
- ReflectPermission
- java.util.PropertyPermission
- java.awt.AWTPermission
- javax.security.auth.AuthPermission
- java.security.
- PermissionCollection (Abstract Class)
- Contains a number of related Permission objects
- Permissions (Object Class)
- Contains a number of PermissionClass objects, sorted in a map by the Class of Permissions they contain
- ProtectionDomain (Object Class)
- Defines a group of classes that are protected with similar permissions
- Policy (Abstract Class)
- Defines the security policy (all permission grants) for the running application
- Contains a number of PermissionCollection objects sored in a map, keyed by their ProtectionDomain
- Determines if proper permissions are available for a given Permission based on its existence in the proper ProtectionDomain
- java.lang.SecurityManager (Object Class)
- Provides permission resolution to the whole program (via System.getSecurityManager()) by acting as the "central point of access control"
- For most permission checks, this class calls out to java.security.AccessController
- SecurityManager can be subclassed and replaced, as described below
- AccessController (Object Class, Singleton)
- Implements access control algorithm
- Also deals with "doPrivileged()"
- When checkPermission() is called, this class unrolls the call stack (using native code), determines all the permissions required, then decides if the call is ok
Guarded Object Classes
Guarded objects are used to pass objects around different access control contexts while maintaining a level of protection. Only code from an appropriate access control context may obtain the associated object.
- GuardedObject (Object Class)
- Used to hold an object and a Guard
- Object can be obtained using the getObject() method - which does a security check using the associated Guard
- Guard (Interface)
- Defines a method to decide if a security check passes
- The method is "public Result evaluate(FSM, Input)" (where FSM is the state machine causing this action, Input is the input that caused the transition)
- Permission (Abstract Class, implements Guard)
- Permission implements Guard by using the SecurityManager (if one exists) to check for this Permission
Using Java Security
Activating the SecurityManager
Applications launched normally (using the java command) do not have security enabled - System.getSecurityManager() will return null, causing all permissions to simply be granted. To turn on the default SecurityManager:
java -Djava.security.manager [Main Class]
To specify your own SecurityManager:
java -Djava.security.manager=[SecurityManager Class] [Main Class]
or, to set it at runtime, use:
SecurityManager sm = new YourSecurityManagerClass(); System.setSecurityManager(sm);
Setting Policy
When Starting the JVM
To set the policy file for the JVM:
java -Djava.security.manager -Djava.security.policy=[URL to policy file]
Using "==" in place of "=" will cause the JVM to ignore other policy files. (not sure what this means...)
By Using a Settings File
Edit ${JAVA_HOME}/lib/security/java.security, add properties in the form "policy.url.n", where n is an integer. The defaults look like this:
policy.url.1=file:${java.home}/lib/security/java.policy
policy.url.2=file:${user.home}/.java.policy
The Policy File
Lot more to learn about this.
There is a tool packaged with Java called policytool that "specifies, generates, edits, exports, and imports a security policies". The user guide is here
References
- An architecture overview - http://articles.techrepublic.com.com/5100-10878_11-6177275.html
- Overview of objects in the security library - http://articles.techrepublic.com.com/5100-10878_11-6178805.html?tag=rbxccnbtr1
- Detailed documentation list - http://java.sun.com/javase/6/docs/technotes/guides/security/index.html
- Details of each of Java's packaged Permission classes - http://java.sun.com/j2se/1.4.2/docs/guide/security/permissions.html
- Tutorials on Security in Java - http://java.sun.com/docs/books/tutorial/security/index.html
- policytool user guide - http://java.sun.com/javase/6/docs/technotes/guides/security/PolicyGuide.html
- Details about the policy file - http://java.sun.com/javase/6/docs/technotes/guides/security/PolicyFiles.html